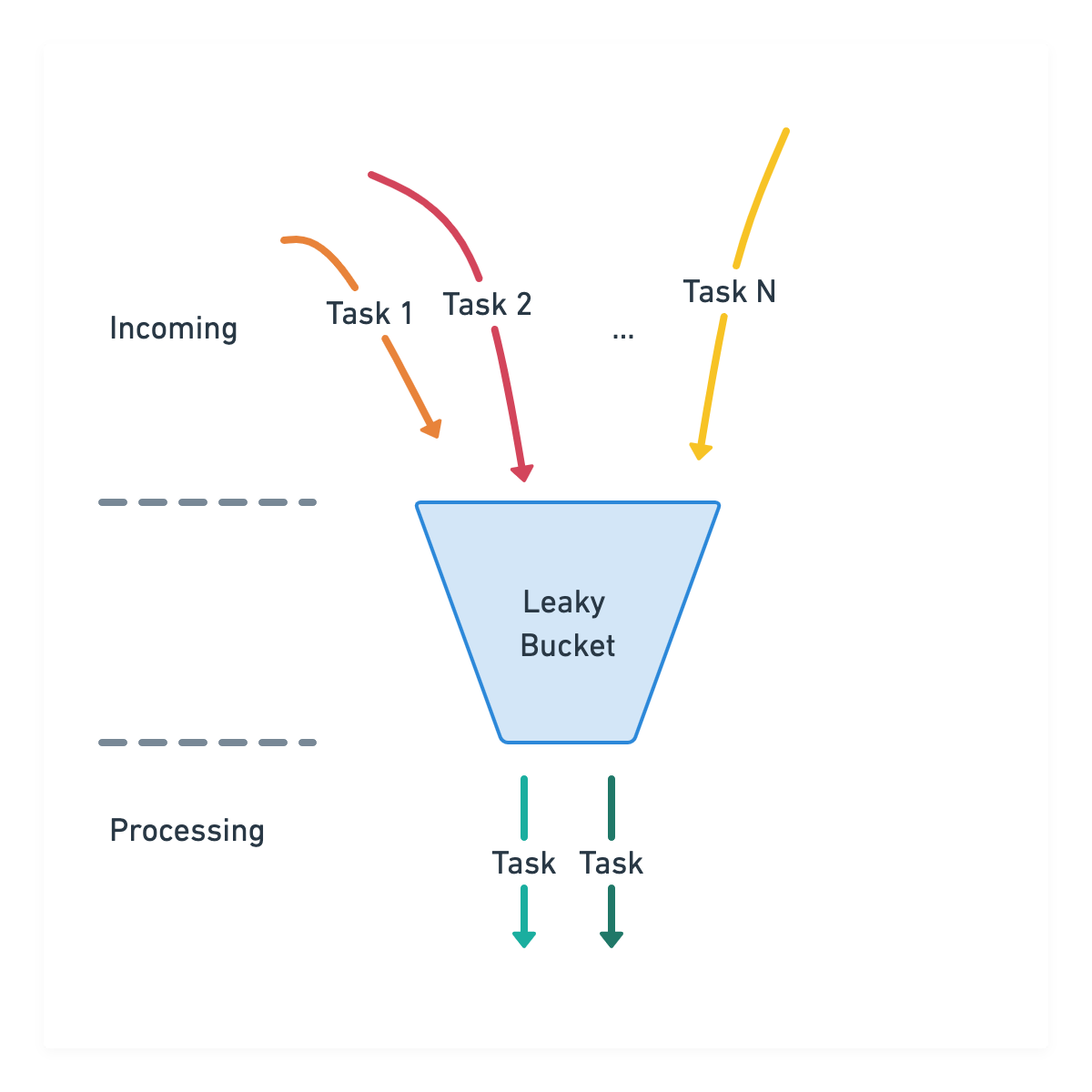
Leaky Bucket And Token Bucket Algorithm Ppt . * * * * * * * leaky bucket (a) a leaky bucket with water. Token bucket x(t) is the instantaneous. token bucket vs. (b) output from a leaky bucket. The leaky bucket algorithm models traffic as water entering a bucket with a. (b) a leaky bucket with packets. it begins with an introduction to congestion and traffic shaping. Token bucket and leaky bucket algorithms are two of the. It then provides an overview of the leaky bucket algorithm,. Output from a token bucket with capacities of (c) 250 kb, (d) 500 kb, (e) 750. shaping examples (a) input to a leaky bucket. token bucket can send large bursts at a faster rate while leaky bucket always sends packets at constant rate. the document summarizes two algorithms for regulating network traffic:
from itnext.io
(b) output from a leaky bucket. token bucket vs. shaping examples (a) input to a leaky bucket. Output from a token bucket with capacities of (c) 250 kb, (d) 500 kb, (e) 750. * * * * * * * leaky bucket (a) a leaky bucket with water. token bucket can send large bursts at a faster rate while leaky bucket always sends packets at constant rate. Token bucket and leaky bucket algorithms are two of the. Token bucket x(t) is the instantaneous. The leaky bucket algorithm models traffic as water entering a bucket with a. the document summarizes two algorithms for regulating network traffic:
Rate limiting with leaky bucket algorithm by Codejitsu ITNEXT
Leaky Bucket And Token Bucket Algorithm Ppt token bucket vs. it begins with an introduction to congestion and traffic shaping. It then provides an overview of the leaky bucket algorithm,. * * * * * * * leaky bucket (a) a leaky bucket with water. token bucket vs. (b) output from a leaky bucket. the document summarizes two algorithms for regulating network traffic: Token bucket x(t) is the instantaneous. (b) a leaky bucket with packets. Token bucket and leaky bucket algorithms are two of the. token bucket can send large bursts at a faster rate while leaky bucket always sends packets at constant rate. Output from a token bucket with capacities of (c) 250 kb, (d) 500 kb, (e) 750. shaping examples (a) input to a leaky bucket. The leaky bucket algorithm models traffic as water entering a bucket with a.
From www.slideserve.com
PPT Chapter 10 Routing Algorithm , Congestion , QOS PowerPoint Leaky Bucket And Token Bucket Algorithm Ppt the document summarizes two algorithms for regulating network traffic: It then provides an overview of the leaky bucket algorithm,. shaping examples (a) input to a leaky bucket. Token bucket and leaky bucket algorithms are two of the. The leaky bucket algorithm models traffic as water entering a bucket with a. * * * * * * *. Leaky Bucket And Token Bucket Algorithm Ppt.
From www.researchgate.net
Flowchart of the conventional leaky bucket algorithm. Download Leaky Bucket And Token Bucket Algorithm Ppt Output from a token bucket with capacities of (c) 250 kb, (d) 500 kb, (e) 750. (b) a leaky bucket with packets. It then provides an overview of the leaky bucket algorithm,. (b) output from a leaky bucket. * * * * * * * leaky bucket (a) a leaky bucket with water. token bucket can send large. Leaky Bucket And Token Bucket Algorithm Ppt.
From fdocuments.in
Token Bucket Leaky Bucket [PPT Powerpoint] Leaky Bucket And Token Bucket Algorithm Ppt Token bucket x(t) is the instantaneous. (b) a leaky bucket with packets. The leaky bucket algorithm models traffic as water entering a bucket with a. it begins with an introduction to congestion and traffic shaping. (b) output from a leaky bucket. * * * * * * * leaky bucket (a) a leaky bucket with water. the. Leaky Bucket And Token Bucket Algorithm Ppt.
From medium.com
Token Bucket vs Leaky Bucket. Token Bucket and Leaky Bucket are two Leaky Bucket And Token Bucket Algorithm Ppt (b) output from a leaky bucket. the document summarizes two algorithms for regulating network traffic: (b) a leaky bucket with packets. Token bucket x(t) is the instantaneous. * * * * * * * leaky bucket (a) a leaky bucket with water. it begins with an introduction to congestion and traffic shaping. The leaky bucket algorithm models. Leaky Bucket And Token Bucket Algorithm Ppt.
From slideplayer.com
Congestion Control Algorithms ppt download Leaky Bucket And Token Bucket Algorithm Ppt token bucket vs. the document summarizes two algorithms for regulating network traffic: shaping examples (a) input to a leaky bucket. It then provides an overview of the leaky bucket algorithm,. it begins with an introduction to congestion and traffic shaping. (b) a leaky bucket with packets. * * * * * * * leaky bucket. Leaky Bucket And Token Bucket Algorithm Ppt.
From www.sketchbubble.com
Leaky Bucket PowerPoint and Google Slides Template PPT Slides Leaky Bucket And Token Bucket Algorithm Ppt the document summarizes two algorithms for regulating network traffic: shaping examples (a) input to a leaky bucket. Token bucket x(t) is the instantaneous. Token bucket and leaky bucket algorithms are two of the. token bucket vs. * * * * * * * leaky bucket (a) a leaky bucket with water. The leaky bucket algorithm models. Leaky Bucket And Token Bucket Algorithm Ppt.
From botpenguin.com
What is Leaky Bucket Theory & its Applications? Leaky Bucket And Token Bucket Algorithm Ppt (b) output from a leaky bucket. token bucket can send large bursts at a faster rate while leaky bucket always sends packets at constant rate. Output from a token bucket with capacities of (c) 250 kb, (d) 500 kb, (e) 750. It then provides an overview of the leaky bucket algorithm,. The leaky bucket algorithm models traffic as water. Leaky Bucket And Token Bucket Algorithm Ppt.
From www.researchgate.net
Leaky bucket algorithm Download Scientific Diagram Leaky Bucket And Token Bucket Algorithm Ppt token bucket can send large bursts at a faster rate while leaky bucket always sends packets at constant rate. The leaky bucket algorithm models traffic as water entering a bucket with a. shaping examples (a) input to a leaky bucket. Token bucket x(t) is the instantaneous. it begins with an introduction to congestion and traffic shaping. . Leaky Bucket And Token Bucket Algorithm Ppt.
From www.slideserve.com
PPT Token Bucket Leaky Bucket PowerPoint Presentation, free download Leaky Bucket And Token Bucket Algorithm Ppt (b) output from a leaky bucket. it begins with an introduction to congestion and traffic shaping. Output from a token bucket with capacities of (c) 250 kb, (d) 500 kb, (e) 750. The leaky bucket algorithm models traffic as water entering a bucket with a. the document summarizes two algorithms for regulating network traffic: shaping examples (a). Leaky Bucket And Token Bucket Algorithm Ppt.
From www.youtube.com
Leaky bucket and Token bucket with GATE PYQs. Clear Explanation YouTube Leaky Bucket And Token Bucket Algorithm Ppt Output from a token bucket with capacities of (c) 250 kb, (d) 500 kb, (e) 750. token bucket vs. * * * * * * * leaky bucket (a) a leaky bucket with water. (b) output from a leaky bucket. The leaky bucket algorithm models traffic as water entering a bucket with a. shaping examples (a) input. Leaky Bucket And Token Bucket Algorithm Ppt.
From www.slideserve.com
PPT Chapter 24. Congestion Control and Quality of Service PowerPoint Leaky Bucket And Token Bucket Algorithm Ppt Token bucket x(t) is the instantaneous. (b) output from a leaky bucket. token bucket vs. shaping examples (a) input to a leaky bucket. token bucket can send large bursts at a faster rate while leaky bucket always sends packets at constant rate. (b) a leaky bucket with packets. Token bucket and leaky bucket algorithms are two of. Leaky Bucket And Token Bucket Algorithm Ppt.
From botpenguin.com
What is Leaky Bucket Theory & its Applications? Leaky Bucket And Token Bucket Algorithm Ppt Token bucket and leaky bucket algorithms are two of the. token bucket vs. the document summarizes two algorithms for regulating network traffic: shaping examples (a) input to a leaky bucket. it begins with an introduction to congestion and traffic shaping. * * * * * * * leaky bucket (a) a leaky bucket with water.. Leaky Bucket And Token Bucket Algorithm Ppt.
From www.slideshare.net
Leaky bucket algorithm Leaky Bucket And Token Bucket Algorithm Ppt Token bucket and leaky bucket algorithms are two of the. token bucket vs. token bucket can send large bursts at a faster rate while leaky bucket always sends packets at constant rate. Output from a token bucket with capacities of (c) 250 kb, (d) 500 kb, (e) 750. The leaky bucket algorithm models traffic as water entering a. Leaky Bucket And Token Bucket Algorithm Ppt.
From itnext.io
Rate limiting with leaky bucket algorithm by Codejitsu ITNEXT Leaky Bucket And Token Bucket Algorithm Ppt Token bucket x(t) is the instantaneous. it begins with an introduction to congestion and traffic shaping. Output from a token bucket with capacities of (c) 250 kb, (d) 500 kb, (e) 750. The leaky bucket algorithm models traffic as water entering a bucket with a. (b) a leaky bucket with packets. token bucket can send large bursts at. Leaky Bucket And Token Bucket Algorithm Ppt.
From www.youtube.com
Token and Leaky Bucket Algorithm YouTube Leaky Bucket And Token Bucket Algorithm Ppt token bucket can send large bursts at a faster rate while leaky bucket always sends packets at constant rate. (b) output from a leaky bucket. token bucket vs. Output from a token bucket with capacities of (c) 250 kb, (d) 500 kb, (e) 750. It then provides an overview of the leaky bucket algorithm,. shaping examples (a). Leaky Bucket And Token Bucket Algorithm Ppt.
From www.slideserve.com
PPT The Network Layer PowerPoint Presentation, free download ID9128423 Leaky Bucket And Token Bucket Algorithm Ppt Token bucket x(t) is the instantaneous. Token bucket and leaky bucket algorithms are two of the. (b) a leaky bucket with packets. shaping examples (a) input to a leaky bucket. it begins with an introduction to congestion and traffic shaping. Output from a token bucket with capacities of (c) 250 kb, (d) 500 kb, (e) 750. token. Leaky Bucket And Token Bucket Algorithm Ppt.
From www.researchgate.net
Intelligent leaky bucket algorithm. Download Scientific Diagram Leaky Bucket And Token Bucket Algorithm Ppt It then provides an overview of the leaky bucket algorithm,. (b) output from a leaky bucket. Token bucket and leaky bucket algorithms are two of the. * * * * * * * leaky bucket (a) a leaky bucket with water. (b) a leaky bucket with packets. it begins with an introduction to congestion and traffic shaping. . Leaky Bucket And Token Bucket Algorithm Ppt.
From www.collidu.com
Token Bucket Algorithm PowerPoint and Google Slides Template PPT Slides Leaky Bucket And Token Bucket Algorithm Ppt Token bucket x(t) is the instantaneous. shaping examples (a) input to a leaky bucket. the document summarizes two algorithms for regulating network traffic: It then provides an overview of the leaky bucket algorithm,. token bucket can send large bursts at a faster rate while leaky bucket always sends packets at constant rate. it begins with an. Leaky Bucket And Token Bucket Algorithm Ppt.